Sign In to Azure: 7 Ultimate Steps for Effortless Access
Want to sign in to Azure but stuck somewhere? Don’t worry — you’re not alone. Millions of users access Microsoft Azure daily, and knowing the right steps makes all the difference. This guide breaks down everything you need to know to sign in to Azure smoothly, securely, and successfully — every single time.
Sign In to Azure: The Complete Step-by-Step Guide

Signing in to Azure is the gateway to managing cloud resources, virtual machines, databases, and enterprise applications. Whether you’re an IT admin, developer, or business user, accessing your Azure portal correctly is essential. The process may seem simple, but nuances like account types, authentication methods, and regional settings can trip up even experienced users.
What You Need Before You Sign In to Azure
Before attempting to sign in, ensure you have the following:
- A valid Microsoft account (MSA) or a work/school account (Azure AD account)
- Internet connection
- Browser compatibility (Chrome, Edge, Firefox, or Safari recommended)
- Correct URL: https://portal.azure.com
Without these basics, you might encounter errors like ‘We can’t sign you in,’ ‘Account not found,’ or ‘This site can’t be reached.’
Step-by-Step Process to Sign In to Azure
Follow these steps carefully to sign in to Azure without issues:
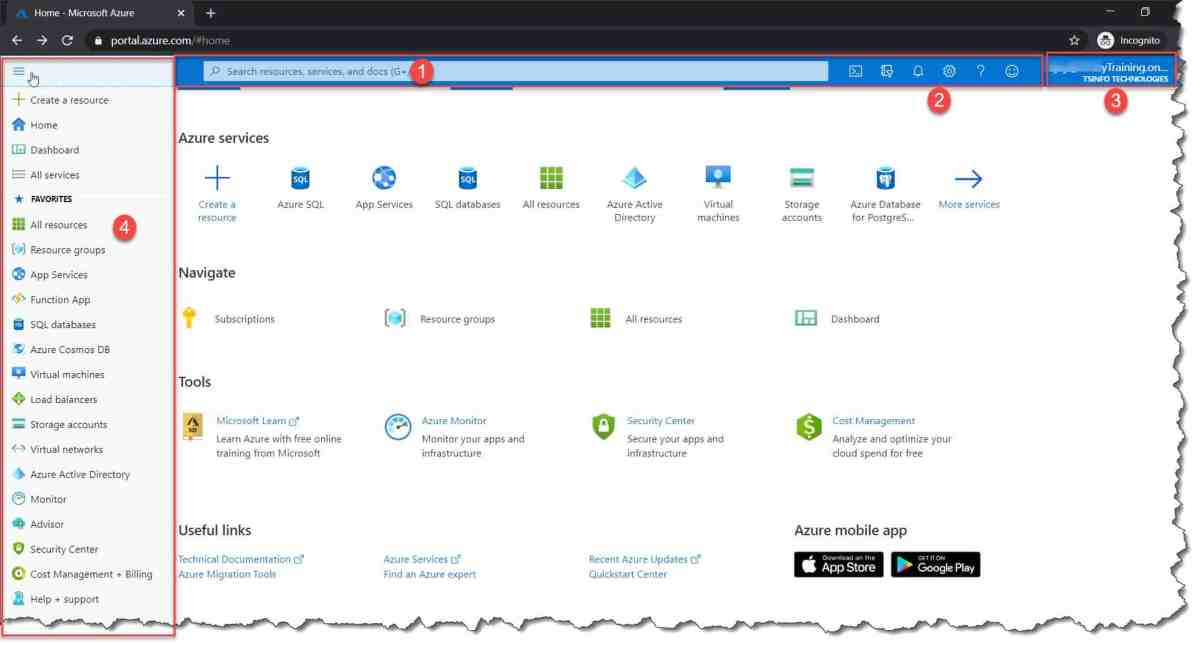
- Open your preferred browser and navigate to Azure Portal.
- Enter your email, phone number, or Skype username linked to your Microsoft or organizational account.
- Click Next.
- Enter your password and click Sign in.
- If multi-factor authentication (MFA) is enabled, complete the verification step (app notification, SMS, or call).
- Upon successful authentication, you’ll be redirected to the Azure dashboard.
It’s crucial to use the correct sign-in URL. Avoid phishing sites by always typing portal.azure.com manually or using a trusted bookmark.
“Security begins at the login screen. A single mistake in authentication can compromise an entire cloud environment.” — Microsoft Azure Security Best Practices Guide
Understanding Azure Account Types for Sign In
Not all accounts are the same when you sign in to Azure. Knowing your account type helps troubleshoot access issues and ensures you’re using the right credentials.
Microsoft Personal Accounts (MSA)
A Microsoft personal account is what you use for services like Outlook.com, Xbox, or Skype. You can use it to sign in to Azure, especially if you’re using Azure for personal projects or free-tier services.
- Emails typically end in @outlook.com, @hotmail.com, or @live.com
- Can be used to create free Azure subscriptions
- Limited administrative capabilities compared to work accounts
While convenient, MSAs are not recommended for enterprise use due to limited governance and compliance features.
Work or School Accounts (Azure AD)
These accounts are managed by organizations through Azure Active Directory (Azure AD). When you sign in to Azure with a work account, you’re accessing resources under your company’s subscription and policies.
- Emails usually follow the format
user@company.com - Administered by IT departments with role-based access control (RBAC)
- Supports advanced security features like conditional access and MFA
Organizations use Azure AD to centralize identity management, making it easier to onboard and offboard employees securely.
Common Issues When Trying to Sign In to Azure
Even with the right credentials, users often face obstacles when trying to sign in to Azure. Let’s explore the most frequent problems and how to resolve them.
Forgot Password or Locked Account
One of the top reasons users can’t sign in to Azure is a forgotten password or a locked account. Azure provides self-service password reset (SSPR) for both personal and organizational accounts.
- Click Forgot password? on the sign-in screen
- Verify your identity via email, phone, or authenticator app
- Set a new password
For work accounts, your organization must have SSPR enabled. Contact your IT administrator if the option isn’t available.
Multi-Factor Authentication (MFA) Failures
MFA is a critical security layer, but it can also be a point of failure. Common MFA issues include:
- Not receiving SMS or call
- Authenticator app not syncing
- Lost or replaced device
To fix MFA issues:
- Ensure your phone has signal or internet access
- Check time synchronization on your device (critical for TOTP codes)
- Use backup methods like app passwords or FIDO2 security keys
Microsoft recommends registering multiple MFA methods to avoid lockout.
Security Best Practices When You Sign In to Azure
Signing in to Azure isn’t just about access — it’s about doing so securely. Cyberattacks often target login portals, making security a top priority.
Enable Multi-Factor Authentication (MFA)
MFA adds an extra verification step beyond your password. Even if your credentials are compromised, attackers can’t access your account without the second factor.
- Use the Microsoft Authenticator app for push notifications
- Set up SMS or voice call as backup
- Consider passwordless options like FIDO2 security keys
According to Microsoft, MFA blocks over 99.9% of account compromise attacks.
Use Conditional Access Policies
For organizations, Conditional Access in Azure AD allows admins to enforce rules based on user location, device compliance, and sign-in risk.
- Block access from untrusted regions
- Require compliant devices for access
- Force MFA for high-risk sign-ins
These policies ensure that even if someone tries to sign in to Azure from a suspicious IP, access is denied or challenged.
“Trust but verify. Conditional Access turns that principle into automated security enforcement.” — Azure Identity Blog
How to Sign In to Azure Using Different Devices
Accessing Azure isn’t limited to desktops. You can sign in to Azure from mobile devices, tablets, and even command-line tools.
Using the Azure Mobile App
The Azure mobile app allows you to monitor resources, receive alerts, and manage services on the go.
- Download the app from Google Play or Apple App Store
- Open the app and tap Sign in
- Enter your credentials and complete MFA
- View dashboards, restart VMs, or check service health
The mobile app is ideal for DevOps teams needing real-time updates without logging into a full desktop session.
Command-Line Access: Azure CLI and PowerShell
For developers and admins, signing in to Azure via CLI or PowerShell is faster and scriptable.
- Install Azure CLI or Azure PowerShell
- Run
az loginorConnect-AzAccount - A browser window opens for authentication
- After successful sign-in, you can run commands
These tools support service principals and managed identities for automated workflows without human interaction.
Managing Multiple Azure Subscriptions When You Sign In
Many users have access to multiple Azure subscriptions — personal, work, client projects, or test environments. Managing them efficiently is key to avoiding confusion and billing errors.
Switching Between Subscriptions
After signing in to Azure, you can switch subscriptions using the portal:
- In the Azure portal, click the subscription filter at the top
- Select the subscription you want to work with
- All resource views will now reflect that subscription
In Azure CLI or PowerShell, use:
az account set --subscription "Subscription Name"Select-AzSubscription -SubscriptionName "Subscription Name"
Understanding Role-Based Access Control (RBAC)
RBAC determines what you can do in each subscription. Common roles include:
- Owner: Full access, including permission management
- Contributor: Can create and manage resources but not assign roles
- Reader: View-only access
Always verify your role in each subscription to avoid permission errors when deploying resources.
Advanced Authentication: Service Principals and Managed Identities
While most users sign in to Azure interactively, automated systems use non-interactive methods like service principals and managed identities.
What Are Service Principals?
A service principal is an identity created for applications, services, or automation tools to access Azure resources.
- Created in Azure AD
- Assigned specific permissions via RBAC
- Used with client secrets or certificates
Example: A CI/CD pipeline uses a service principal to deploy an app to Azure App Service.
Managed Identities for Seamless Access
Managed identities eliminate the need to manage credentials for apps running in Azure.
- System-assigned: Tied to a specific resource (e.g., VM)
- User-assigned: Can be shared across multiple resources
- Automatically handles authentication to Azure services
For example, an Azure Function with a managed identity can securely access Azure Key Vault without storing secrets in code.
“Managed identities reduce the attack surface by removing hardcoded credentials.” — Microsoft Azure Architecture Center
Troubleshooting: What to Do If You Can’t Sign In to Azure
Despite best efforts, sign-in failures happen. Here’s a systematic approach to diagnosing and fixing them.
Check Your Internet and DNS Settings
Basic connectivity issues can prevent access to portal.azure.com.
- Test your internet connection
- Try accessing Azure from a different network
- Flush DNS cache (
ipconfig /flushdnson Windows)
Sometimes corporate firewalls or DNS policies block Azure endpoints.
Clear Browser Cache and Cookies
Corrupted browser data can interfere with Azure authentication.
- Clear cache and cookies for
portal.azure.comandlogin.microsoftonline.com - Try an incognito or private browsing session
- Use a different browser to isolate the issue
This often resolves issues like infinite redirects or ‘Session expired’ errors.
Contact Your Administrator or Microsoft Support
If self-help fails, escalate the issue:
- Contact your organization’s Azure admin — they can check account status, MFA registration, and Conditional Access policies
- For billing or subscription issues, reach out to Microsoft Azure Support
- Use the Azure Status page to check for service outages
Never share your password or MFA codes with anyone, even if they claim to be from Microsoft.
Why can’t I sign in to Azure even with the right password?
Several factors could prevent sign-in despite correct credentials: multi-factor authentication failure, account lockout, Conditional Access policies blocking access, browser issues, or service outages. Check the Azure Status page and try signing in from a different device or browser.
Can I use a personal Microsoft account to sign in to Azure?
Yes, you can use a personal Microsoft account (like Outlook.com) to sign in to Azure and create a free account. However, for business or enterprise use, a work or school account (Azure AD) is recommended for better security, compliance, and management.
What should I do if I lose my MFA device?
If you lose your MFA device, use backup methods like SMS, phone call, or a secondary authenticator app. If none are available, contact your Azure administrator to reset your MFA settings or use the self-service password reset portal if enabled.
How do I sign in to Azure CLI without a browser?
You can use device code flow for headless authentication. Run az login --use-device-code, then visit https://microsoft.com/devicelogin on another device, enter the code, and authenticate. This is useful for servers or VMs without GUI access.
Is it safe to sign in to Azure on public computers?
No, it’s not recommended. Public computers may have keyloggers or session hijacking risks. If you must, use private browsing mode, avoid saving credentials, and sign out completely afterward. Better yet, use Azure’s mobile app or a trusted personal device.
Signing in to Azure is more than just entering a username and password — it’s the first line of defense in your cloud security strategy. From choosing the right account type to enabling MFA and troubleshooting access issues, every step matters. Whether you’re a beginner or a seasoned pro, mastering the sign-in process ensures you can manage your cloud resources efficiently and securely. By following the best practices outlined in this guide, you’ll minimize downtime, prevent unauthorized access, and make the most of Microsoft Azure’s powerful capabilities. Stay vigilant, stay authenticated, and keep your cloud journey smooth.
Recommended for you 👇
Further Reading: