Azure Portal Log In: 7 Ultimate Tips for Effortless Access
Logging into the Azure portal is your first step into a world of cloud power. Whether you’re managing virtual machines, monitoring resources, or deploying apps, mastering the Azure portal log in process is essential. Let’s dive into everything you need to know to access your Microsoft Azure environment smoothly, securely, and without hassle.
Azure Portal Log In: Understanding the Basics

The Azure portal is Microsoft’s web-based interface for managing cloud services. To access it, users must perform an Azure portal log in using valid credentials tied to a Microsoft Entra ID (formerly Azure Active Directory). This centralized dashboard allows administrators and developers to control resources across global data centers.
What Is the Azure Portal?
The Azure portal is a comprehensive management console that provides a graphical user interface (GUI) for interacting with Microsoft Azure services. From creating storage accounts to configuring virtual networks, the portal simplifies complex cloud operations. It’s accessible from any modern browser, making it a go-to tool for IT professionals and developers alike.
- Web-based interface for managing Azure resources
- Available at portal.azure.com
- Supports role-based access control (RBAC) and multi-factor authentication (MFA)
Why Is Logging In Crucial?
Every Azure portal log in is a gateway to your cloud infrastructure. Secure access ensures that only authorized personnel can modify critical systems. A failed or compromised login can lead to service disruption or data breaches. Therefore, understanding the login mechanism is not just about convenience—it’s a cornerstone of cloud security.
“Access control begins at the login screen. In cloud environments like Azure, a secure login is the first line of defense.” — Microsoft Security Best Practices
Step-by-Step Guide to Azure Portal Log In
Performing an Azure portal log in is straightforward, but knowing the correct steps helps avoid common pitfalls. Whether you’re a new user or a seasoned admin, following this guide ensures a smooth entry into your Azure environment.
Navigate to the Official Login Page
Always start by visiting the official Azure portal URL: https://portal.azure.com. Avoid third-party links or search engine results that may lead to phishing sites. Bookmarking the official site is a best practice for security and convenience.
- Ensure the URL is correct and uses HTTPS
- Check for the padlock icon in the browser address bar
- Avoid clicking on suspicious ads claiming to be the Azure login page
Enter Your Credentials
After reaching the portal, enter your email address associated with your Azure subscription. This is typically a work or school account (e.g., user@company.com), not a personal Microsoft account unless specifically configured. After entering the email, click ‘Next’ and input your password.
- Use a strong, unique password
- Ensure Caps Lock is off
- Double-check your username spelling
Complete Multi-Factor Authentication (MFA)
If MFA is enabled—which it should be—you’ll be prompted to verify your identity using a second method. This could be a notification on the Microsoft Authenticator app, a phone call, or a text message with a code. This step significantly enhances the security of your Azure portal log in.
- Push notifications are the fastest and most secure MFA method
- Backup methods like SMS or phone calls are useful if the primary method fails
- Administrators can configure MFA policies via Azure AD
Common Issues During Azure Portal Log In and How to Fix Them
Even with a simple process, users often encounter issues during Azure portal log in. These can range from forgotten passwords to account lockouts. Understanding these problems and their solutions can save time and reduce frustration.
Forgot Password or Locked Account
One of the most frequent issues is forgetting your password or getting locked out after multiple failed attempts. Azure provides a self-service password reset (SSPR) feature that allows users to regain access without administrator intervention.
- Click ‘Forgot password?’ on the login screen
- Follow the prompts to verify identity via email, phone, or security questions
- Set a new, strong password
Organizations should ensure SSPR is enabled in Azure AD to minimize helpdesk tickets. More information can be found in Microsoft’s official guide on password reset registration.
Sign-In Errors and Their Meanings
Azure displays specific error messages during login attempts. Understanding these helps in quick troubleshooting. For example:
- Error 50076: Requires multi-factor authentication. Complete MFA to proceed.
- Error 53003: Access denied due to Conditional Access policies. Contact your admin.
- Error 50126: Invalid username or password. Recheck credentials.
Microsoft maintains a comprehensive list of AADSTS error codes to help diagnose authentication issues.
Browser and Cache Issues
Sometimes, the problem isn’t with Azure but with your browser. Cached credentials, outdated cookies, or disabled JavaScript can block a successful Azure portal log in.
- Clear browser cache and cookies
- Try an incognito or private browsing window
- Ensure JavaScript is enabled
- Update your browser to the latest version
If issues persist, try using a different browser like Chrome, Edge, or Firefox. Microsoft recommends using the latest version of Microsoft Edge for optimal performance.
Security Best Practices for Azure Portal Log In
Security is paramount when dealing with cloud infrastructure. Every Azure portal log in should be protected with robust measures to prevent unauthorized access and potential breaches.
Enable Multi-Factor Authentication (MFA)
MFA is one of the most effective ways to secure your Azure portal log in. It adds an extra verification layer beyond just a password. Even if a password is compromised, attackers can’t access the account without the second factor.
- Use the Microsoft Authenticator app for push notifications
- Register multiple MFA methods as backups
- Enforce MFA for all users, especially administrators
According to Microsoft, MFA can block over 99.9% of account compromise attacks. Learn more at Microsoft’s MFA documentation.
Use Conditional Access Policies
Conditional Access in Azure AD allows organizations to enforce access controls based on user location, device compliance, risk level, and more. For example, you can block logins from certain countries or require compliant devices for access.
- Create policies that require MFA for external access
- Block legacy authentication protocols
- Require device compliance for high-risk applications
These policies are configured under Azure AD > Security > Conditional Access. Proper setup ensures that every Azure portal log in meets organizational security standards.
Monitor Sign-In Logs and Alerts
Azure provides detailed sign-in logs that help detect suspicious activity. By reviewing these logs, administrators can identify failed login attempts, unusual locations, or impossible travel patterns.
- Access logs via Azure AD > Monitoring > Sign-in logs
- Set up alerts for multiple failed sign-ins
- Integrate with Azure Monitor or Microsoft Sentinel for advanced threat detection
Regularly auditing sign-in activity is a proactive way to maintain the integrity of your Azure portal log in process.
Alternative Methods for Azure Portal Log In
While the standard web login is the most common, Azure supports several alternative methods for accessing the portal, especially useful in automation, scripting, or high-security environments.
Using Azure CLI for Authentication
The Azure Command-Line Interface (CLI) allows users to log in via the terminal. This method is popular among developers and DevOps engineers who prefer scripting over GUI interactions.
- Run
az loginin your terminal - Follow the device code flow: visit microsoft.com/devicelogin and enter the code
- Authenticate using your Azure credentials
This method supports both user and service principal logins. More details are available in the Azure CLI authentication guide.
Logging In with Service Principals
Service principals are Azure AD objects used by applications, services, or automation tools to access Azure resources. They allow non-interactive Azure portal log in scenarios, such as CI/CD pipelines.
- Create a service principal via Azure portal or CLI
- Assign roles using RBAC
- Use client ID and secret (or certificate) for authentication
While service principals don’t log in to the portal directly, they authenticate API calls and scripts that interact with Azure resources.
Single Sign-On (SSO) Integration
Organizations using identity providers like Okta, Ping Identity, or on-premises Active Directory Federation Services (AD FS) can enable SSO for Azure. This allows users to log in once and access multiple applications, including the Azure portal, without re-entering credentials.
- Configure SSO via Azure AD > Enterprise Applications
- Supports SAML, OAuth, and OpenID Connect
- Improves user experience and reduces password fatigue
SSO is especially valuable in large enterprises with complex identity management needs.
Managing Multiple Subscriptions During Azure Portal Log In
Many users have access to multiple Azure subscriptions—perhaps for different departments, projects, or clients. Managing these efficiently after an Azure portal log in is crucial for productivity and access control.
Switching Between Subscriptions
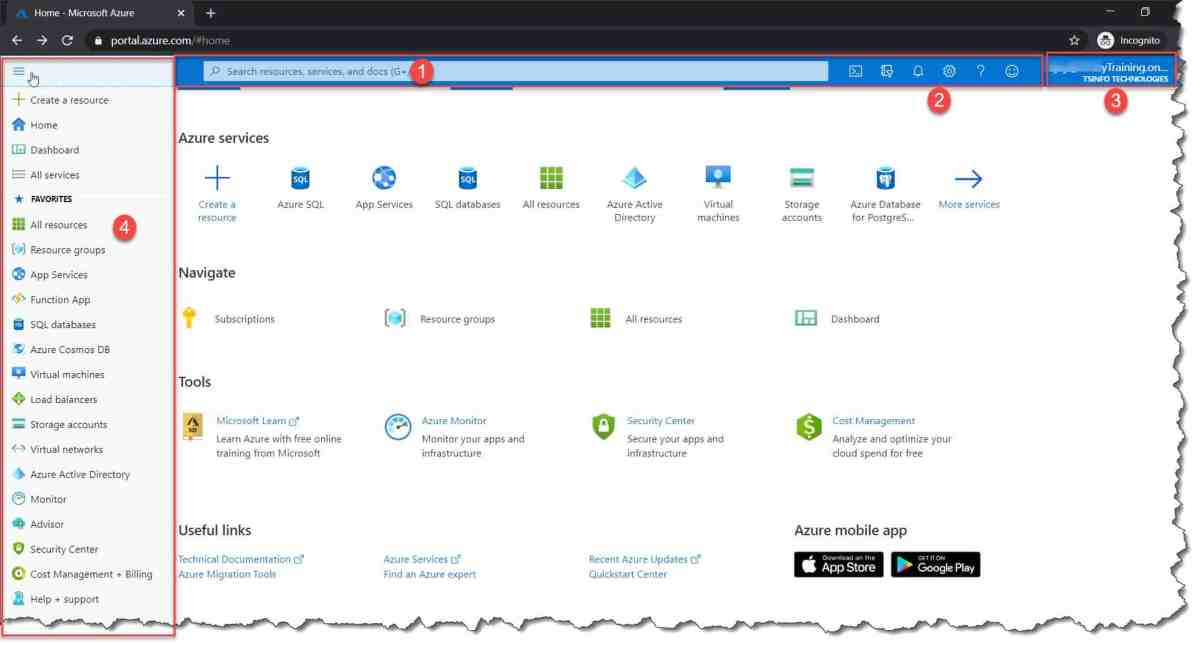
After logging in, you can switch between subscriptions using the directory + subscription selector in the top-right corner of the portal. This dropdown lets you change both your Azure AD directory and the active subscription.
- Click your profile icon in the top-right
- Select ‘Switch directory’ or ‘Change subscription’
- Choose the desired subscription from the list
This feature is essential for consultants or IT teams managing resources across multiple accounts.
Understanding Role-Based Access Control (RBAC)
RBAC determines what actions a user can perform within a subscription. After Azure portal log in, your permissions are enforced based on assigned roles like Owner, Contributor, or Reader.
- Owners can manage everything, including access
- Contributors can create and manage resources but not grant access
- Readers can view resources but not make changes
Administrators can assign roles via Azure > Subscriptions > Access control (IAM).
Using Azure Lighthouse for Cross-Tenant Management
Azure Lighthouse enables service providers to manage multiple customer tenants from a single interface. After logging into their own tenant, providers can access delegated resources across customers without switching accounts manually.
- Customers delegate specific resources to the provider
- Provider accesses resources via ‘My Customers’ in the Azure portal
- Enhances scalability and operational efficiency
This is a game-changer for MSPs (Managed Service Providers) offering Azure management services.
Optimizing the Azure Portal Log In Experience
Beyond security and functionality, the user experience matters. A smooth Azure portal log in process improves productivity and reduces support overhead.
Customizing the Portal Dashboard
After logging in, users can personalize their dashboard by pinning frequently used resources, creating custom blades, and organizing widgets. This reduces navigation time and streamlines workflows.
- Pin VMs, storage accounts, or monitoring tools to the dashboard
- Resize and rearrange tiles for optimal layout
- Save custom views for different roles or projects
A well-organized dashboard makes the post-login experience more efficient.
Using Browser Extensions and Tools
Several browser extensions enhance the Azure portal experience. For example, the Azure SDK team provides tools for developers, and third-party extensions offer dark mode, keyboard shortcuts, or resource tagging helpers.
- Dark mode extensions reduce eye strain during long sessions
- Keyboard shortcut tools speed up navigation
- Tagging assistants help maintain resource governance
Always ensure extensions are from trusted sources to avoid security risks.
Enabling Passwordless Authentication
Microsoft is pushing toward a passwordless future. Users can now log in using the Microsoft Authenticator app, Windows Hello, or FIDO2 security keys—eliminating the need for passwords altogether.
- Register a security key or enable biometric login
- Authenticate with a simple tap or fingerprint
- Reduces phishing and credential theft risks
Passwordless authentication is supported in Azure AD and can be configured under Security > Authentication methods. Learn more at Microsoft’s passwordless guide.
What should I do if I can’t log in to the Azure portal?
First, check your internet connection and ensure you’re using the correct URL: portal.azure.com. Verify your credentials and try resetting your password if needed. If MFA is required, ensure your authentication method is working. Clear your browser cache or try a different browser. If the issue persists, contact your Azure administrator or consult Microsoft’s troubleshooting guide.
Can I use a personal Microsoft account to log in to Azure?
Yes, but only if it has been added to an Azure AD tenant or granted access to a subscription. Most enterprise scenarios use work or school accounts (Azure AD accounts), while personal accounts are typically used for individual developers or free tier access.
How do I enable MFA for my Azure portal log in?
MFA can be enabled by the user or enforced by an administrator. Users can go to myaccount.microsoft.com and set up additional security verification. Administrators can enforce MFA via Azure AD > Security > Multi-factor authentication or through Conditional Access policies.
What is the difference between Azure AD and a Microsoft account?
Azure AD (now Microsoft Entra ID) is an enterprise identity service used for organizational accounts, supporting features like MFA, Conditional Access, and RBAC. A Microsoft account is a personal account (e.g., @outlook.com) used for consumer services like OneDrive or Xbox. Azure portals typically use Azure AD accounts for management.
Is it safe to log in to the Azure portal on public Wi-Fi?
It’s not recommended unless you’re using a VPN. Public Wi-Fi networks are vulnerable to eavesdropping. Even with MFA, your session could be at risk. Always use secure, private networks when performing an Azure portal log in, especially for administrative tasks.
Mastering the Azure portal log in process is more than just entering a username and password—it’s about security, efficiency, and control. From understanding the basics to implementing MFA and exploring alternative authentication methods, every step enhances your cloud experience. By following best practices and staying informed, you ensure that your access to Azure remains both seamless and secure. Whether you’re a beginner or an expert, optimizing your login strategy is a critical part of effective cloud management.
Recommended for you 👇
Further Reading: