Azure Log In: 7 Ultimate Tips for Secure & Fast Access
Logging into Azure doesn’t have to be complicated. Whether you’re a developer, IT admin, or business owner, mastering the azure log in process is your first step toward seamless cloud management. Let’s break it down—simply, securely, and smartly.
Understanding Azure Log In: The Gateway to Microsoft Cloud

The azure log in process is more than just typing a username and password. It’s the critical entry point to Microsoft Azure, one of the world’s most powerful cloud computing platforms. Millions of users rely on Azure for virtual machines, data storage, AI tools, and enterprise applications. A secure and efficient login experience ensures uninterrupted access to these services.
What Is Azure Log In?
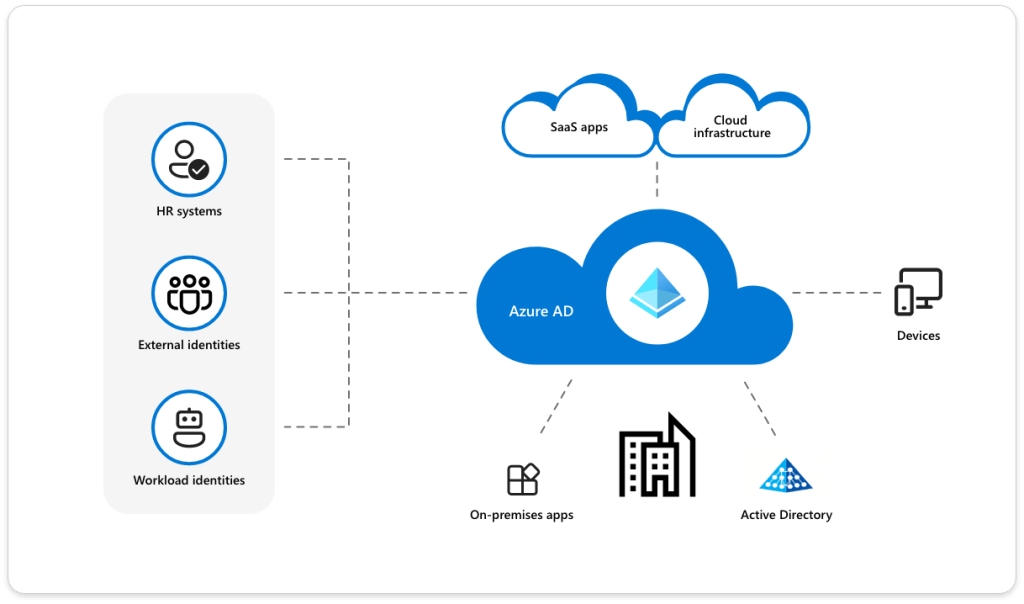
Azure log in refers to the authentication process that grants users access to the Microsoft Azure portal, Azure CLI, Azure PowerShell, or any Azure-integrated service. This process typically involves a Microsoft account (MSA) or a work or school account managed through Azure Active Directory (Azure AD).
- Users can log in via portal.azure.com, the official entry point.
- Authentication is managed through Azure AD, which supports multi-factor authentication (MFA), conditional access, and identity protection.
- The login experience varies based on user role, subscription type, and security policies.
Why Azure Log In Matters for Businesses
In today’s hybrid and remote work environments, secure access to cloud resources is non-negotiable. A compromised azure log in can lead to data breaches, service disruptions, or unauthorized access to critical infrastructure.
“Over 90% of enterprise cloud breaches begin with compromised credentials.” — Microsoft Digital Defense Report, 2023
Therefore, understanding how to securely perform an azure log in isn’t just technical—it’s strategic.
Azure Log In Methods: Choosing the Right Path
There are multiple ways to perform an azure log in, each suited to different use cases. Knowing which method to use can save time, reduce errors, and enhance security.
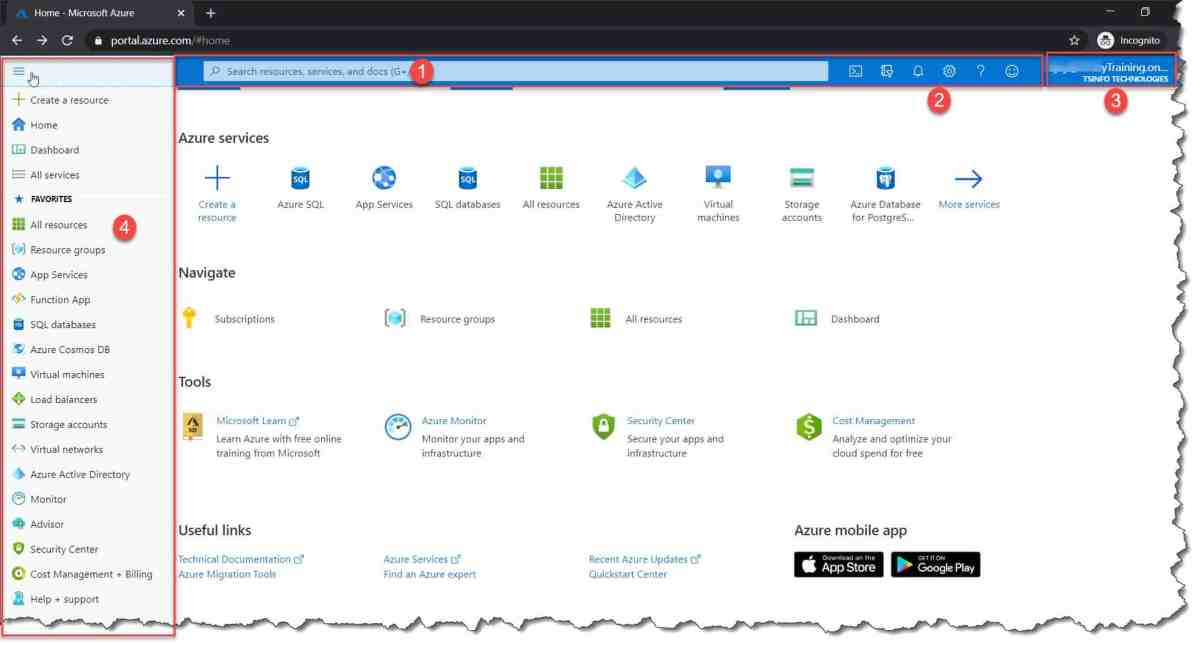
Web Portal Login (portal.azure.com)
The most common method is logging in through the Azure web portal. This is ideal for administrators managing resources via a graphical interface.
- Navigate to portal.azure.com and enter your email address.
- Enter your password and complete any additional verification steps (e.g., MFA).
- Once authenticated, you’ll land on the Azure dashboard with access to your subscriptions and services.
This method is user-friendly and perfect for beginners or occasional users.
Azure CLI and PowerShell Login
For developers and DevOps engineers, command-line tools like Azure CLI and Azure PowerShell offer faster, scriptable access.
- Run
az loginin your terminal to initiate the azure log in via CLI. - You’ll be prompted to open microsoft.com/devicelogin and enter a code.
- After successful authentication, the CLI stores your session context for subsequent commands.
This method supports automation and integration into CI/CD pipelines, making it essential for infrastructure-as-code workflows.
Service Principal and Managed Identities
For applications and services running in Azure, using a service principal or managed identity is the secure way to handle azure log in without human intervention.
- A service principal is an identity created for an app in Azure AD, allowing it to access Azure resources.
- Managed identities are automatically managed by Azure and eliminate the need to store credentials.
- These are crucial for serverless functions, VMs, and microservices requiring secure, automated access.
Microsoft recommends using managed identities over service principals whenever possible to reduce credential exposure.
Step-by-Step Guide to Azure Log In for Beginners
If you’re new to Azure, the login process might seem overwhelming. Here’s a clear, step-by-step guide to help you complete your first azure log in successfully.
Step 1: Navigate to the Azure Portal
Open your preferred web browser and go to portal.azure.com. This is the official Microsoft Azure portal and the primary interface for managing cloud resources.
- Ensure you’re using a secure, updated browser (Chrome, Edge, or Firefox recommended).
- Avoid public or shared computers for initial logins to prevent session hijacking.
Step 2: Enter Your Credentials
Type in your email address associated with your Azure account. This could be:
- A personal Microsoft account (e.g., @outlook.com, @hotmail.com).
- A work or school account provided by your organization (e.g., user@company.com).
After entering your email, click “Next” and input your password. If you’ve enabled passwordless options like Windows Hello or FIDO2 keys, you may be prompted to use those instead.
Step 3: Complete Multi-Factor Authentication (MFA)
Most Azure accounts require MFA for added security. After entering your password, you’ll be prompted to verify your identity through one of the following:
- Microsoft Authenticator app notification or code.
- Text message or phone call to a registered number.
- Security key (e.g., YubiKey).
- Biometric verification on supported devices.
Once verified, you’ll gain access to the Azure dashboard. You can choose to mark this device as trusted to reduce future MFA prompts.
Troubleshooting Common Azure Log In Issues
Even with a well-configured account, users often encounter issues during the azure log in process. Understanding common problems and their solutions can save hours of frustration.
Forgot Password or Locked Account
One of the most frequent issues is forgetting your password or getting locked out due to multiple failed attempts.
- Click “Forgot password?” on the login screen to reset it.
- If using a work account, contact your organization’s IT admin for a password reset.
- Ensure your recovery email or phone number is up to date in Azure AD.
Microsoft’s self-service password reset (SSPR) feature can help users regain access without admin intervention.
Multi-Factor Authentication Failures
MFA is a security cornerstone, but it can also be a point of failure.
- If you’ve lost your authenticator device, use backup methods like SMS or alternate email.
- Ensure your Microsoft Authenticator app is synced and time is accurate.
- Admins can temporarily disable MFA for emergency access (not recommended long-term).
Microsoft recommends registering at least two MFA methods to avoid lockout scenarios.
Region or Tenant Access Errors
Sometimes, users see errors like “You don’t have access to this tenant” or “Subscription not found.” This usually happens due to:
- Logging into the wrong Azure portal instance (e.g., public vs. government cloud).
- Being assigned to multiple tenants and selecting the incorrect one.
- Permissions not properly assigned by the admin.
To resolve this, ensure you’re logging into the correct environment (e.g., portal.azure.us for Azure Government) and verify your role assignments in Azure AD.
Enhancing Security During Azure Log In
Security should never be an afterthought. The azure log in process is a prime target for phishing, brute force attacks, and credential stuffing. Implementing advanced security measures is essential.
Enable Multi-Factor Authentication (MFA)
MFA adds a second layer of verification, making it significantly harder for attackers to gain access even if they have your password.
- Go to Azure AD > Security > Multi-Factor Authentication to configure it.
- Enforce MFA for all users, especially admins.
- Use phishing-resistant methods like FIDO2 security keys for highest protection.
According to Microsoft, MFA can block over 99.9% of account compromise attacks.
Implement Conditional Access Policies
Conditional Access allows you to set rules that control how and when users can perform an azure log in.
- Require MFA when logging in from untrusted locations.
- Block access from certain countries or IP ranges.
- Enforce device compliance (e.g., only allow logins from managed, encrypted devices).
These policies are configured in the Azure AD portal under “Conditional Access” and are vital for zero-trust security models.
Use Passwordless Authentication
Microsoft is pushing toward a passwordless future. You can now use Windows Hello, FIDO2 keys, or the Microsoft Authenticator app to eliminate passwords entirely.
- Users register their biometric or security key in the Microsoft account settings.
- During azure log in, they verify via their registered method instead of typing a password.
- This reduces phishing risk and improves user experience.
Adopting passwordless authentication is a powerful step toward modern identity security.
Best Practices for Managing Azure Log In at Scale
For organizations with dozens or thousands of users, managing azure log in efficiently is critical. Poor identity management can lead to security gaps, compliance violations, and operational inefficiencies.
Centralize Identity with Azure Active Directory
Azure AD is the backbone of identity management in Azure. It allows centralized control over user accounts, groups, and access policies.
- Create groups based on roles (e.g., Admins, Developers, Finance) for easier permission management.
- Use Single Sign-On (SSO) to reduce the number of logins users need to remember.
- Synchronize on-premises Active Directory with Azure AD using Azure AD Connect.
Centralized identity reduces administrative overhead and improves security posture.
Leverage Role-Based Access Control (RBAC)
RBAC ensures users only have the permissions they need—no more, no less.
- Assign built-in roles like “Reader,” “Contributor,” or “Owner” based on responsibility.
- Create custom roles for specialized access requirements.
- Regularly audit role assignments to remove unnecessary permissions.
Principle of least privilege is key to minimizing insider threats and lateral movement in case of a breach.
Monitor and Audit Log In Activities
Visibility into who is logging in, when, and from where is crucial for security and compliance.
- Use Azure Monitor and Azure Log Analytics to track sign-in logs.
- Set up alerts for suspicious activities (e.g., logins from unusual locations).
- Export logs to a SIEM system like Microsoft Sentinel for advanced threat detection.
Regular audits help detect anomalies early and support forensic investigations if needed.
Advanced Azure Log In Scenarios
Beyond basic login, Azure supports complex authentication scenarios for enterprise and hybrid environments. Understanding these can help you design more robust access strategies.
Federated Identity with SAML or OAuth
Organizations often use federated identity to integrate Azure with existing identity providers like ADFS, Okta, or Ping Identity.
- SAML 2.0 allows users to log in via their corporate identity system.
- OAuth 2.0 and OpenID Connect are used for app-level authentication.
- Federation enables seamless SSO across on-premises and cloud apps.
This is especially useful for large enterprises with legacy systems.
Guest User Access and B2B Collaboration
Azure supports inviting external users (partners, vendors, clients) as guest users in your directory.
- Send an invitation via email; the guest logs in with their own identity.
- They can access specific resources without needing a new password.
- Admins retain control over access duration and permissions.
This is ideal for cross-organizational projects and secure collaboration.
Hybrid Identity with Azure AD Connect
For companies with on-premises infrastructure, Azure AD Connect bridges the gap between local AD and cloud identity.
- Synchronizes user accounts, passwords, and group memberships.
- Supports pass-through authentication and password hash sync.
- Enables seamless azure log in for users regardless of location.
This hybrid approach provides flexibility without sacrificing security.
Future of Azure Log In: Trends and Innovations
The way we authenticate to Azure is evolving rapidly. Microsoft is investing heavily in identity innovation to stay ahead of cyber threats and improve user experience.
Azure AD Identity Protection
This service uses AI to detect risky sign-ins and compromised users.
- It analyzes login patterns, device health, and IP reputation.
- Automatically blocks or requires additional verification for suspicious attempts.
- Integrates with Conditional Access for real-time policy enforcement.
Identity Protection is a game-changer for proactive security.
Passwordless and Biometric Log In
Microsoft is pushing for a world without passwords. Features like Windows Hello, FIDO2 keys, and the Microsoft Authenticator app are leading this shift.
- Users can log in using facial recognition, fingerprints, or security keys.
- Eliminates password reuse and phishing risks.
- Improves accessibility and user satisfaction.
Organizations adopting passwordless see fewer helpdesk calls and stronger security.
Zero Trust and Continuous Authentication
The future of azure log in isn’t just about the initial login—it’s about continuous verification.
- Zero Trust assumes no user or device is trusted by default.
- Continuous authentication monitors behavior during the session.
- If risk is detected, access can be revoked in real time.
Microsoft’s Zero Trust model is becoming the standard for enterprise security.
What if I can’t log in to Azure even after resetting my password?
If you’ve reset your password but still can’t log in, check if your account is locked, disabled, or assigned to the wrong tenant. Clear your browser cache, try a private/incognito window, or use a different device. If the issue persists, contact your Azure administrator or Microsoft Support for assistance.
How do I enable MFA for my Azure account?
Go to the Azure portal, navigate to Azure Active Directory > Security > Multi-Factor Authentication. Select your user account and enable MFA. Follow the prompts to register your preferred verification method. For organizations, use Conditional Access policies to enforce MFA across all users.
Can I use the same Microsoft account for personal and Azure log in?
Yes, you can use a personal Microsoft account (e.g., @outlook.com) to log in to Azure, especially for free trials or individual subscriptions. However, for business use, Microsoft recommends using a work or school account managed through Azure AD for better security and control.
What is the difference between Azure AD and Microsoft Account?
A Microsoft Account (MSA) is a personal account for consumer services like Outlook, Xbox, or OneDrive. Azure AD is an enterprise identity service for business applications and cloud resources. While both can be used for azure log in, Azure AD offers advanced management, security, and integration features for organizations.
How can I automate Azure log in for scripts and CI/CD pipelines?
Use service principals or managed identities for automated access. Create a service principal in Azure AD, assign it the necessary roles, and use its credentials (client ID and secret) in your scripts. For enhanced security, prefer managed identities, which don’t require storing secrets and are automatically rotated by Azure.
Mastering the azure log in process is essential for anyone using Microsoft’s cloud platform. From basic web portal access to advanced identity management, every step impacts security, efficiency, and user experience. By following best practices—enabling MFA, using conditional access, adopting passwordless methods, and monitoring sign-ins—you can ensure a secure and smooth login experience. As Azure continues to evolve, staying updated on authentication trends like Zero Trust and AI-driven protection will keep your organization ahead of threats. Whether you’re a solo developer or managing a global enterprise, a solid understanding of azure log in is your foundation for cloud success.
Further Reading: